
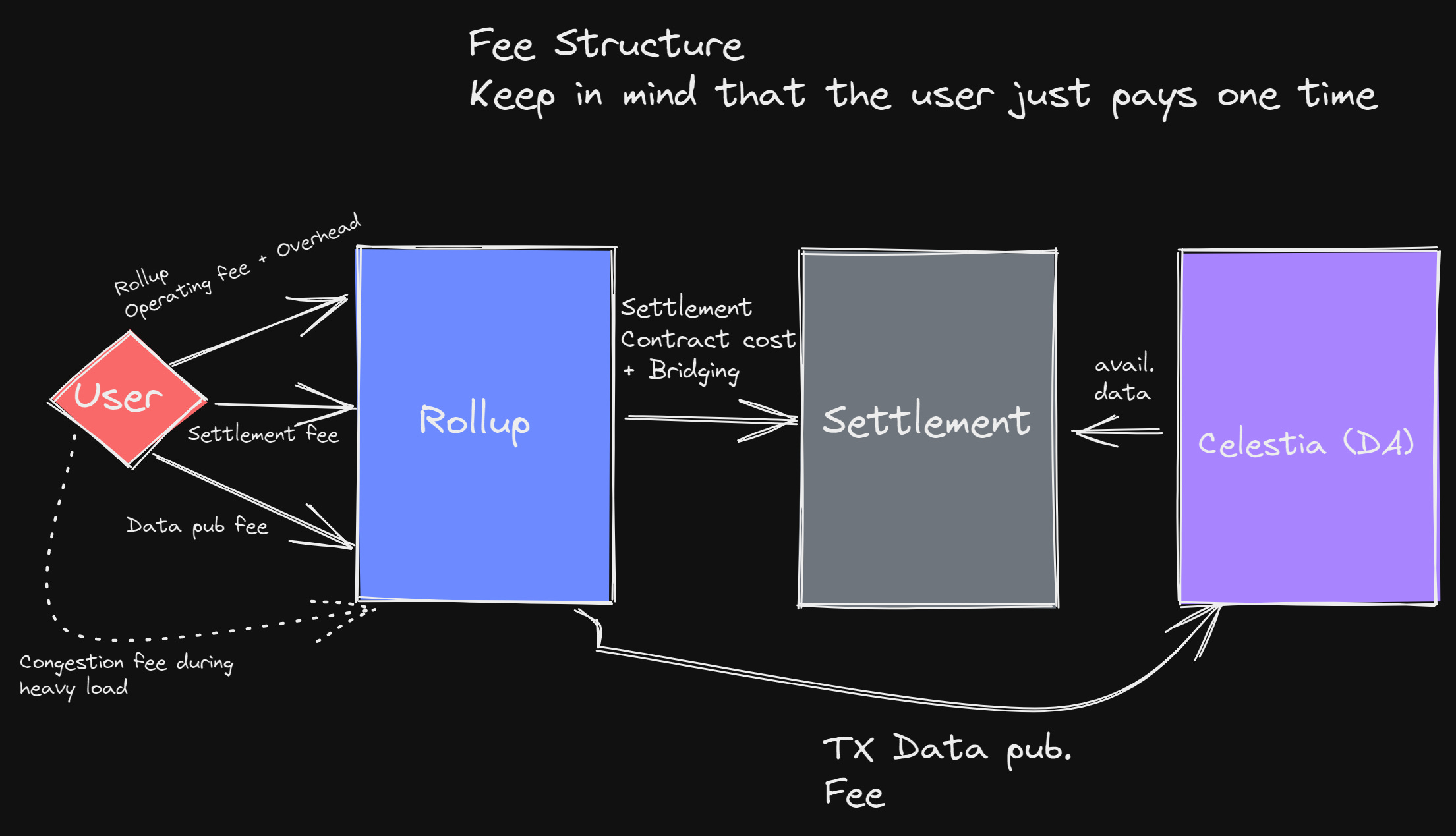
In the evolving landscape of modular blockchains, provable data availability stands as a linchpin for scalability and security. As projects push the boundaries of what decentralized networks can do, the need to guarantee that all transaction data is genuinely accessible to validators, rollups, and light clients has never been more critical. This is where erasure coding steps in as a game-changer for DA (data availability) layers.

Erasure Coding: The Backbone of Modern Data Availability
Erasure coding is not just another buzzword in blockchain circles; it’s a mathematical technique with decades of proven utility in distributed systems. By slicing data into fragments and adding redundancy, erasure codes ensure that the original dataset can be reconstructed even if some pieces are lost or withheld. In the context of modular blockchains, this means that even if certain nodes go offline or act maliciously, the network can still provably access all transaction data.
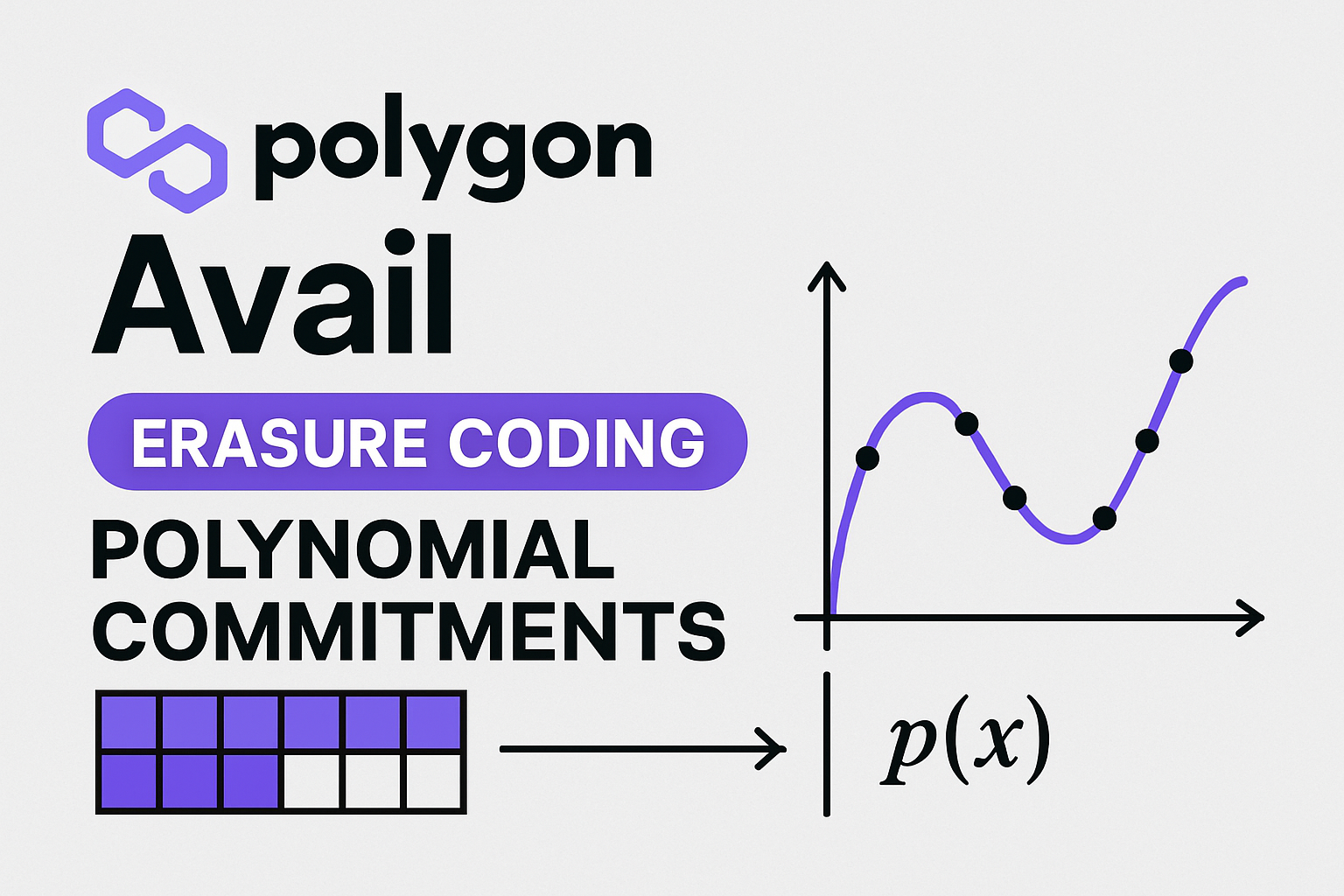
Leading DA layers like Celestia and Polygon Avail have implemented advanced erasure coding schemes, such as two-dimensional Reed-Solomon codes, to encode each block’s data. This approach allows nodes to reconstruct full blocks from partial samples, drastically reducing the bandwidth required for light clients while maintaining high confidence in data integrity.
Key Benefits of Erasure Coding in Blockchain DA Layers
-
Enhanced Data Availability: Erasure coding allows block data to be reconstructed even if some fragments are missing, ensuring that all transaction data remains accessible to the network—even in the presence of faulty or malicious nodes.
-
Efficient Storage Utilization: By splitting data into shards with minimal redundancy, erasure coding reduces the overall storage burden on each node compared to full data replication, optimizing resource usage across the network.
-
Robust Security Against Data Withholding: Techniques like Data Availability Sampling (DAS) in Celestia and matrix encoding in Polygon Avail make it extremely difficult for malicious actors to hide or withhold data without detection, strengthening the integrity of the blockchain.
-
Scalability for Modular Blockchains: Erasure coding supports the separation of execution and data availability layers, enabling modular blockchain architectures to scale efficiently while maintaining high throughput and reliability.
-

Light Client Verification: Erasure-coded data enables light clients to verify data availability by sampling only small portions of blocks, as demonstrated by Celestia, reducing bandwidth requirements and improving accessibility for a wider range of users.
-
Resilience Without Honest Majority Assumptions: Solutions like Polygon Avail use erasure coding and polynomial commitments to guarantee data availability without relying on the assumption that most nodes are honest, increasing trustlessness and decentralization.
-
Protection Against Data Availability Attacks: Innovations such as Coded Merkle Trees (CMTs) combine erasure coding with Merkle proofs, providing constant-cost protection and allowing secure verification even if the majority of nodes are adversarial.
How Modular Blockchains Leverage Erasure Coding
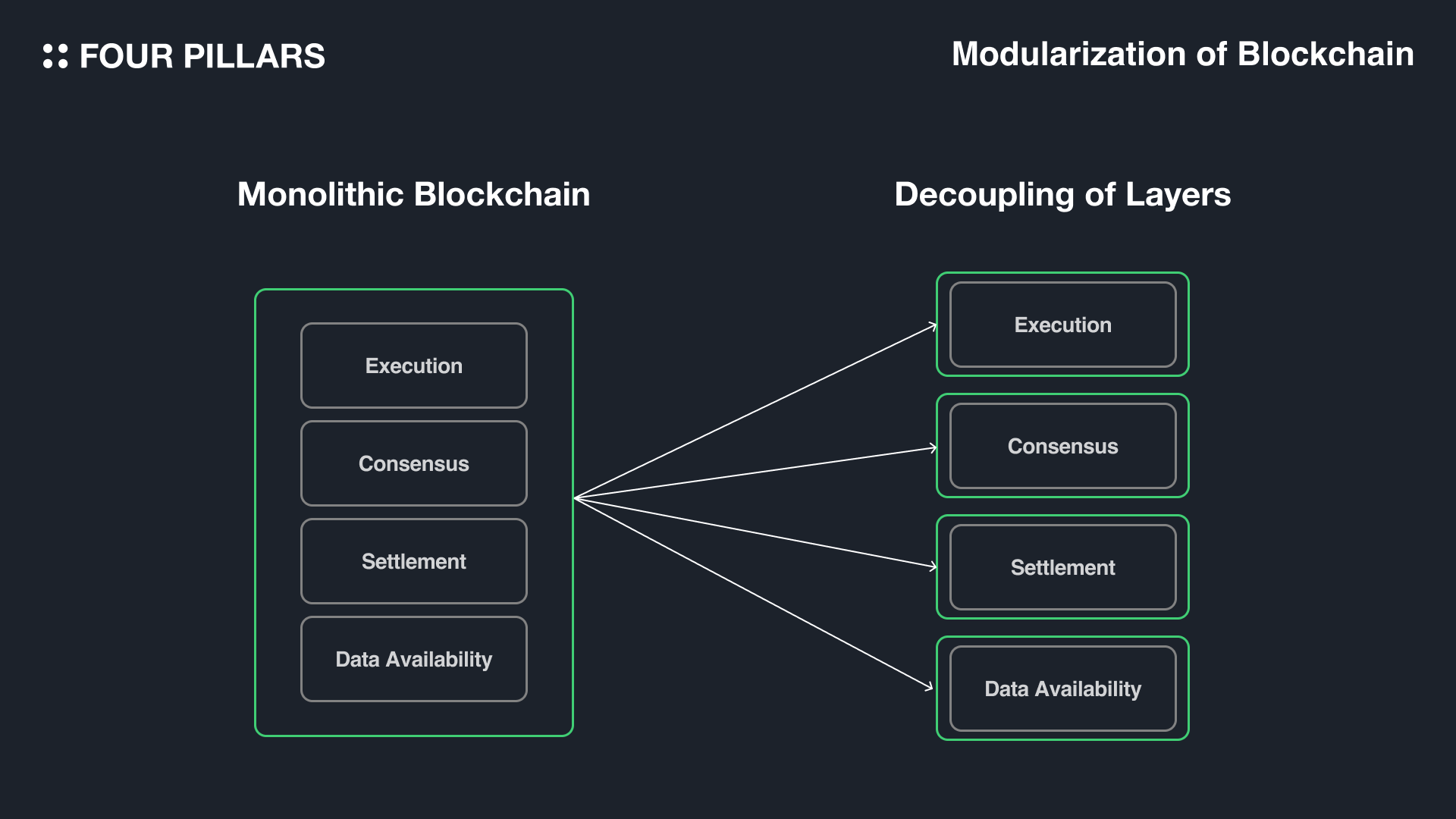
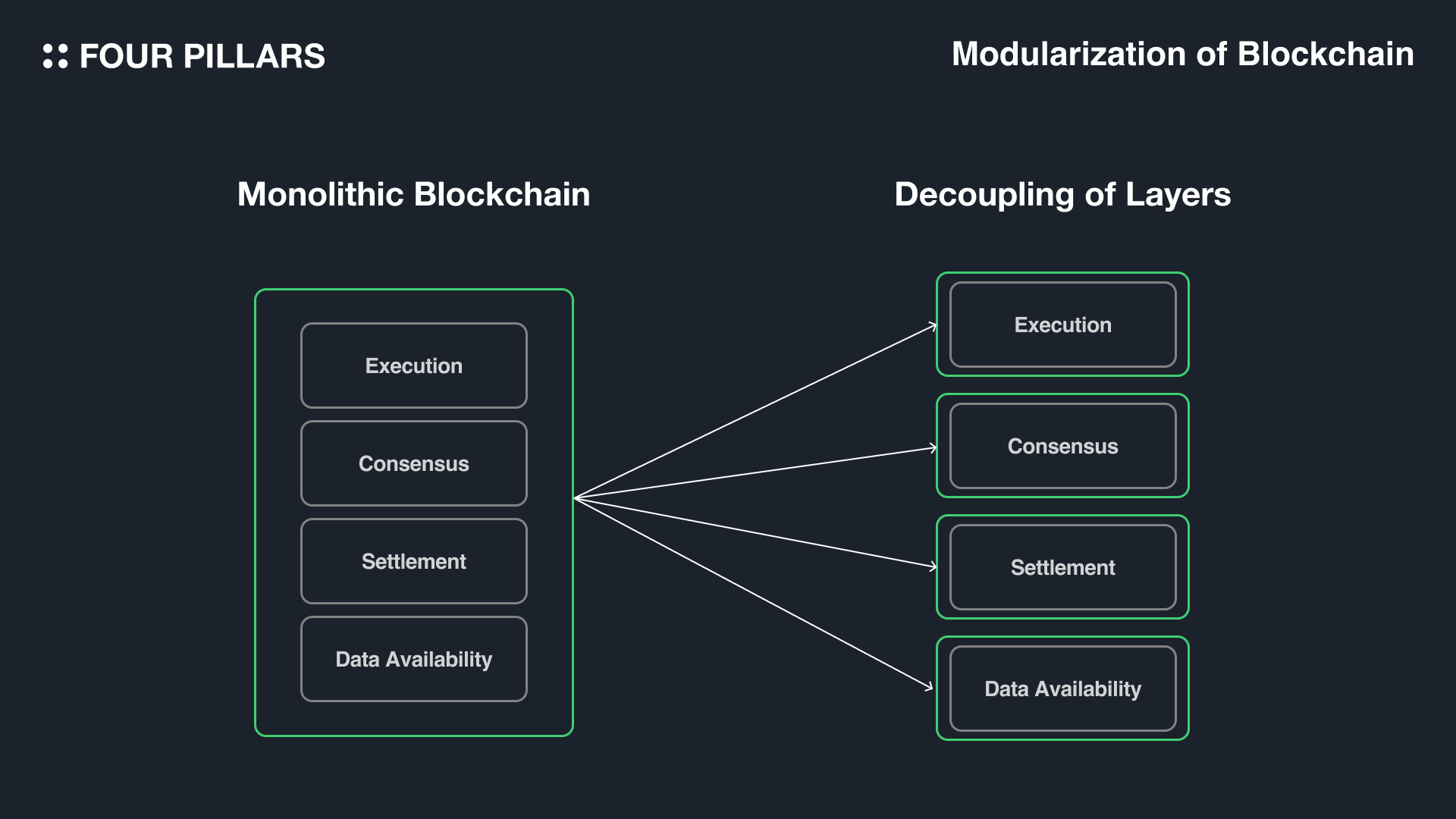
The shift toward modularity separates execution from data availability and consensus, creating specialized layers optimized for each function. In this architecture, DA layers act as dedicated memory banks for transaction data, making it crucial that any actor can independently verify that all block data is available without trusting centralized entities.
This is achieved through protocols where block producers encode transaction data using erasure codes before publishing it to the network. Light clients then perform data availability sampling: instead of downloading entire blocks, they randomly sample small portions. If enough samples are available and valid, statistical guarantees ensure the whole dataset hasn’t been withheld or censored.
The innovation doesn’t stop there. Recent research into Coded Merkle Trees (CMTs) combines sparse erasure codes with Merkle proofs, allowing nodes to verify full block availability by downloading only a logarithmic number of bytes relative to total block size, a massive efficiency gain over naive approaches.
Pioneers: Celestia, Polygon Avail and Beyond
Celestia, one of the first purpose-built modular blockchains, employs two-dimensional Reed-Solomon erasure coding coupled with Data Availability Sampling (DAS). This combination empowers even lightweight devices to validate that all necessary information is accessible, without needing to trust full nodes or download gigabytes of raw block data.
Polygon Avail pushes this further by integrating Kate polynomial commitments into its matrix-based encoding scheme. Here, hiding even a single transaction would require withholding a significant portion of an entire block, making censorship both detectable and costly.
The bottom line: these solutions prove that robust provable data availability isn’t science fiction, it’s already being deployed at scale by projects at the bleeding edge of Web3 infrastructure.
As the modular blockchain stack matures, the synergy between erasure coding and proof-of-availability protocols is setting new standards for network resilience. The field is rapidly advancing, with projects like EigenDA and 0G Labs fine-tuning coding efficiency and retrieval guarantees to push DA performance even further. Innovations such as network coding and Coded Merkle Trees are closing the gap between theoretical security and practical, scalable deployments.
Critically, these advances aren’t just academic. They’re addressing real-world pain points for rollups, dApps, and cross-chain bridges that demand bulletproof guarantees of data integrity. In practice, erasure-coded DA layers offer a path to trust-minimized interoperability, where any execution environment can reliably verify its data roots without reliance on monolithic blockchains or centralized sequencers.
What Makes Provable Data Availability So Transformative?
Let’s break down why erasure coding is now at the core of every serious modular DA layer:
Transformative Features of Provable Data Availability in Modular Blockchains
-
Erasure Coding for Redundancy and Recovery: Modular blockchains like Celestia and Polygon Avail use erasure coding to split and encode data into fragments, adding redundancy. This ensures that the full dataset can be reconstructed even if some fragments are missing, dramatically increasing resilience against node failures or malicious actors.
-
Data Availability Sampling (DAS): Celestia pioneered DAS, allowing light clients to verify data availability by randomly sampling small portions of encoded block data. This drastically reduces resource requirements for verification while maintaining high confidence in data availability.
-
Matrix-Based Data Arrangement: Polygon Avail arranges block data into a two-dimensional matrix and applies erasure coding column-wise. Combined with polynomial commitments, this design makes it nearly impossible for sequencers to hide transactions without detection, eliminating reliance on fraud proofs or honest majority assumptions.
-

Coded Merkle Trees (CMT): CMTs integrate erasure coding with Merkle trees, enabling constant-cost protection against data availability attacks—even if most nodes are malicious. Nodes can verify full block availability by downloading a compact hash commitment and sampling a logarithmic number of bytes, enhancing both efficiency and security.
-
Separation of Data Availability from Execution: Platforms like Celestia and EigenDA decouple the data availability layer from execution and settlement. This modularity allows for independent scaling, greater flexibility, and the ability for multiple blockchains to leverage a shared, robust data availability layer.
By providing mathematical certainty that all transaction data is accessible, even when some nodes are faulty or adversarial, erasure coding enables permissionless innovation at scale. This means Layer 2s can publish proofs with confidence, validators can participate without running full nodes, and users gain stronger censorship resistance.
The Road Ahead: From Theory to Ubiquity
The next wave of modular blockchains will likely build on these foundations with even more efficient encoding schemes and cross-layer optimizations. Expect further improvements in bandwidth usage, faster sampling algorithms for light clients, and tighter integration of provable DA into rollup-centric architectures.
For developers evaluating DA solutions today, the message is clear: provable data availability powered by erasure coding isn’t just a technical upgrade, it’s a paradigm shift that unlocks new levels of scalability and composability across ecosystems. Watch closely as emerging protocols like EigenDA and 0G Labs compete to set benchmarks for throughput, reliability, and trustless access to blockchain data.
The future of modular blockchain scalability hinges on robust DA layers, and erasure coding is the engine driving this evolution.






